Phishing attacks are serious cybersecurity threats that can suddenly affect any business, no matter their size or location. Fraudsters are constantly coming up with new ways to try to infiltrate businesses, and it only takes one click to allow them access. There are many different types of phishing. For instance, “whaling” is when a scammer targets senior executives, “smishing” is when a criminal uses text messages, and an “angler” attack includes posting fake links on social media or stalking a victim’s social profiles to learn more about them before sending a fake email. Any of these phishing attacks can lead to what this article focuses on, which is known as Business Email Compromise (BEC).
Business Email Compromise (BEC)
According to the FBI’s Internet Crime Report, “In 2022, the FBI’s Internet Crime Complaint Center (IC3) received 21,832 BEC complaints with adjusted losses over $2.7 billion.” A BEC is a type of phishing attack in which a criminal uses a compromised or fake email address of an executive, coworker, or vendor to send a request asking the recipient (likely an employee) to provide funds or other sensitive information. The severity of damage can range from relatively mild (buying a few hundred dollars in giftcards) to financially damaging (sending thousands of dollars to pay a fake invoice) to severe reputation, money, and/or client loss (allowing a scammer to gain access to client’s bank or investment information).
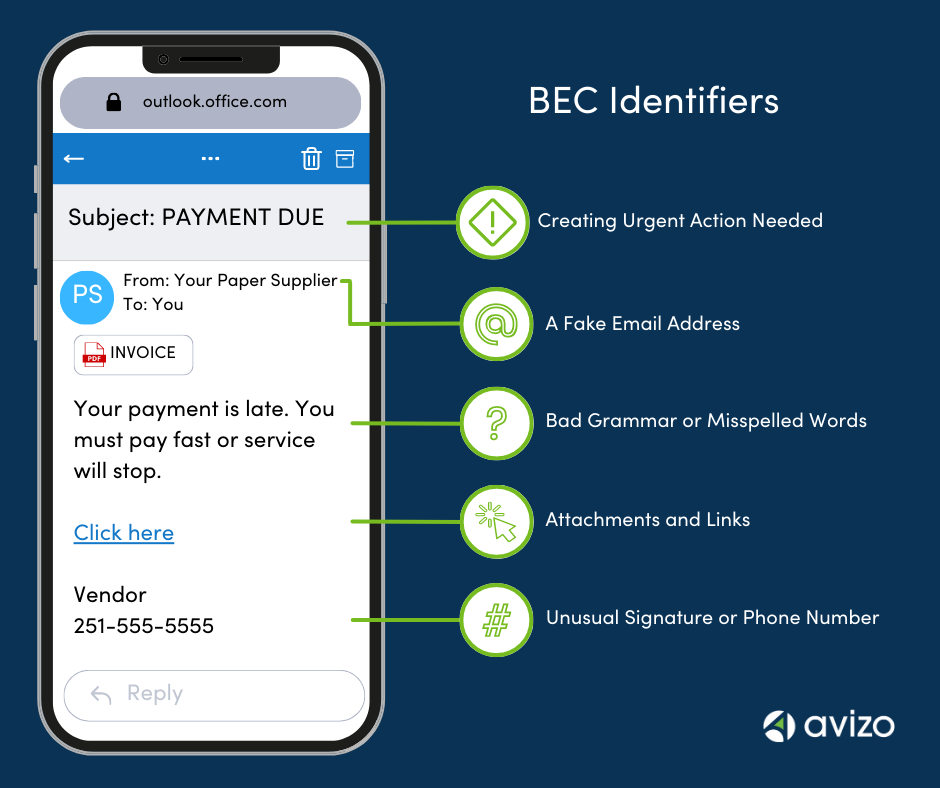
5 Ways to Spot a Business Email Compromise Attempt
Scammers use urgency (and sometimes threats) to get you to take action before thinking about the task or asking questions.
The name of the sender may appear to be correct, but you should check the sender’s full email address by either clicking it or hovering your mouse over it. A scammer often uses a slight variation of the legitimate email address to fool you into thinking the fake account is real.
Aside from urgency, poor grammar or bad spelling can be a tip off that an email is fake. Scam emails are generally written using a translator tool, so if the message is short, uses strange words, or has errors, it’s likely a scam.
Attachments and links are where malware can be hidden. You should never click on a link or download an attachment if you notice any red flags in an email. The malware will download and silently watch legitimate company email threads to gain access to other sensitive data.
Check the signature line and compare it to an email you know is legitimate. The fake email line might sign the name differently and will contain a fake phone number. If you call the number, you’ll be talking to a scammer.
Steps to Take When You Get a Suspicious Message
The simplest thing to do when you receive an email that looks suspicious is to pick up the phone and call the person who “sent” it. It’s better to take an extra minute or two to double check the legitimacy of an urgent task than to risk your organization’s finances and reputation. Here are a few tips on what you should and should not do when you receive a phishy-looking email.
Don’t give into the “urgency” of the request. Take the time to scroll over the name of the sender, or click on it to show the entire email address. Examine it carefully to see if it’s correct.
Call the “sender” using a number you have called before or have on legitimate email/bill. Ask them to confirm if they made the request.
If you suspect a message is a scam, it’s a good idea to alert others on your team who may receive it as well. This will help ensure no one clicks on any malicious links or attachments.
If you have an IT team, you can ask them to inspect the message for legitimacy. If you confirm the email is a scam, you can also report it to the FBI’s IC3.
If the email seems suspicious at all, do not open any attachments or click on any links within the message. (The only thing you CAN click is the name to view the whole email address.)
You should call the “sender” – but do not use any numbers provided in the email. Use a number you have called before or have on legitimate email/bill.
Responding to the email will not cause any immediate harm, but if you respond, the scammer may email you back to try to continue the scam. It’s better to just report and delete the message.
Your Best BEC Protection
The best defense for any organization is to have an official Cybersecurity policy along with training so your entire team is educated. If you would like to learn more about Cybersecurity training options, we can recommend some options for you to consider.

Chris VanArsdale
Chris is a Strategic Analyst who maintains expertise in litigation support, international taxation, and complex entity and fiduciary taxation services.